PENETRATION TESTING
 Penetration testing is the process of investigating and finding holes in the IT infrastructure of an organization, by attempting maneuvers used by malicious attackers. In a few words penetration testing shows business owners, decision makers and especially IT personnel, the steps they need to undertake in order to provide security to their users and data.
Penetration testing is the process of investigating and finding holes in the IT infrastructure of an organization, by attempting maneuvers used by malicious attackers. In a few words penetration testing shows business owners, decision makers and especially IT personnel, the steps they need to undertake in order to provide security to their users and data.
There are a number of reasons to conducting penetration tests and they help not only secure the infrastructure but also safeguard an organization’s employees, their data, credentials and their corporate privacy. Such reasons include preventing data breaches, testing how strong the existing security framework of the organization is, and ensuring that new applications which are to be included in the infrastracture are secure and the employees are using them in a safe manner and accordingly to the organization’s security policies.
Furthermore, the most important reason for going ahead with penetration testing is to ensure that your IT security team will be prepared to take some relevant and required steps and measures towards defending your infrastructure against intruders, denial of service attackers, phishing attempts, or even against social engineering attacks against a company’s personnel.
A typical penetration test goes through these stages:
Goal: Setting the objective of the security assessment.
Reconnaissance: Finding out as much as possible about the target company and the systems being audited. This occurs both online and offline.
Discovery: Port or vulnerability scanning of the IP ranges in question to learn more about the environment.
Exploitation: Using the knowledge of vulnerabilities and systems to exploit systems to gain access, either at the operating system or application level.
Brute forcing: Testing all systems for weak passwords and gaining access if they do.
 Websites and web applications are usually the easiest way for people to find your company and learn information about it. It is beneficial for any organization to have a strong online presence, while also reducing the possibility of the website being penetrated and having protected directories stolen or exposed. It is also considered dangerous for an organization to suffer a website defacement, which is an attack that changes a website visually, or even a contextual defacement which maliciously changes the information visitors can gain through visiting the website. Furthermore, attackers can upload malware and spyware such as viruses and trojan horses, which can easily infect visitors if they are not adequately protected themselves.
Websites and web applications are usually the easiest way for people to find your company and learn information about it. It is beneficial for any organization to have a strong online presence, while also reducing the possibility of the website being penetrated and having protected directories stolen or exposed. It is also considered dangerous for an organization to suffer a website defacement, which is an attack that changes a website visually, or even a contextual defacement which maliciously changes the information visitors can gain through visiting the website. Furthermore, attackers can upload malware and spyware such as viruses and trojan horses, which can easily infect visitors if they are not adequately protected themselves.
Web applications are a major point of vulnerability in organizations today. Web app holes have resulted in the theft of millions of credit cards, major financial and reputational damage for hundreds of enterprises, and even the compromise of thousands of browsing machines that visited Web sites altered by attackers.
Information Gathering
Often analysis of the infrastructure and topology architecture can reveal a great deal about a web application. Information such as source code, HTTP methods permitted, administrative functionality, authentication methods, and infrastructural configurations can be obtained.
Authentication is the act of establishing or confirming something (or someone) as authentic, that is, that claims made by or about the thing are true. Authenticating an object may mean confirming its provenance, whereas authenticating a person often consists of verifying her identity. Authentication depends upon one or more authentication factors. In computer security, authentication is the process of attempting to verify the digital identity of the sender of a communication. A common example of such a process is the logon process. Testing the authentication schema means understanding how the authentication process works and using that information to circumvent the authentication mechanism.
At the core of any web-based application is the way in which it maintains state and thereby controls user-interaction with the site. Session Management broadly covers all controls on a user from authentication to leaving the application. HTTP is a stateless protocol, meaning that web servers respond to client requests without linking them to each other. Even simple application logic requires a user’s multiple requests to be associated with each other across a “session”. This necessitates third party solutions – through either Off-The-Shelf (OTS) middleware and web server solutions, or bespoke developer implementations. Most popular web application environments, such as ASP and PHP, provide developers with built-in session handling routines. Some kind of identification token will typically be issued, which will be referred to as a “Session ID” or Cookie. There are a number of ways in which a web application may interact with a user. Each is dependent upon the nature of the site, the security, and availability requirements of the application. Whilst there are accepted best practices for application development, such as those outlined in the OWASP Guide to Building Secure Web Applications, it is important that application security is considered within the context of the provider’s requirements and expectations.
Authorization is the concept of allowing access to resources only to those permitted to use them. Testing for Authorization means understanding how the authorization process works, and using that information to circumvent the authorization mechanism. Authorization is a process that comes after a successful authentication, so the tester will verify this point after he holds valid credentials, associated with a well-defined set of roles and privileges. During this kind of assessment, it should be verified if it is possible to bypass the authorization schema, find a path traversal vulnerability, or find ways to escalate the privileges assigned to the tester.
Business logic can have security flaws that allow a user to do something that isn’t allowed by the business. For example, if there is a limit on reimbursement of $1000, could an attacker misuse the system to request more money than it is intended? Or, perhaps, users are supposed to do operations in a particular order, but an attacker could invoke them out of sequence. Or can a user make a purchase for a negative amount of money? Frequently, these business logic checks simply are not present in the application.
The most common web application security weakness is the failure to properly validate input coming from the client or environment before using it. This weakness leads to almost all of the major vulnerabilities in web applications, such as cross site scripting, SQL injection, interpreter injection, locale/Unicode attacks, file system attacks, and buffer overflows.
The HTTP clear-text protocol is normally secured via an SSL or TLS tunnel, resulting in HTTPS traffic. In addition to providing encryption of data in transit, HTTPS allows the identification of servers (and, optionally, of clients) by means of digital certificates. We test for both weak SSL/TSL ciphers and SSL certificate validity for both client side and server side.
In a network environment there are not only dangers from the outside, but equal or sometimes higher and more important dangers within a network’s perimeter. Most attacks of today are delivered upon via the sending of phishing emails or cross-site scripting attacks which allow attacker with access to an organization’s internal network. During an Internal PenTest, we try to gain unauthorized access to the internal systems of an organization and try to exploit physical entities such as routers, firewalls, applications as well as the organization’s employees through social networking.
We assess issues such as clear text passwords, shared accounts and database accessibility from within the internal network. Finally we work with clients to set objectives in order to help them come to a sufficient security compliance level, and allow them and their employees to understand the dangers of not following industry standard secure practices. Furthermore, this procedure will allow us and the client to be prepared when deploying future applications, installations or employment of new personnel to do so in a secure manner which will not compromise the internal network and through it allow access to unauthorized persons, thus relieving the stress of protecting sensitive information and personal data.
- Services Probing
- Exploit Research
- Manual Vulnerability Testing and Verification of Identified Vulnerabilities
- Intrusion Detection/Prevention System Testing
- Password Service Strength Testing
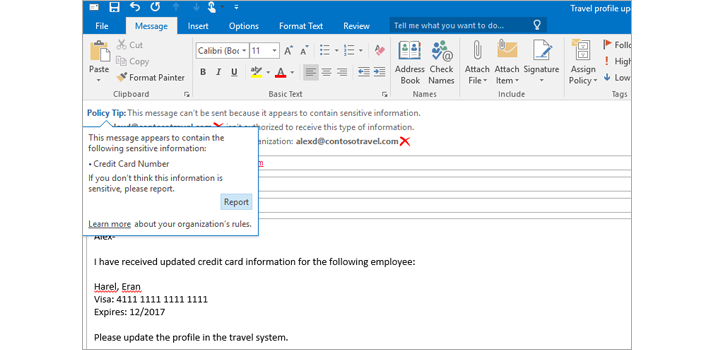
Exchange helps protect business communication and sensitive information, simplifying internal and regulatory compliance. Built-in defenses against viruses, spam, and phishing attacks actively protect your communications. Data loss prevention features identify, monitor, and protect sensitive data through deep content analysis, and Policy Tips in Outlook inform users about policy violations before sensitive data is sent. Your compliance officers can run In-Place eDiscovery across Exchange, SharePoint, and Skype for Business from the eDiscovery Center Tooltip with availability of eDiscovery in select Office 365 plans to identify, hold, and analyze your organization’s data. The data always remains in place, so you never have to manage a separate store of data.
